What happened?
On December 9th, an acute remote code execution (RCE) vulnerability was reported in the Apache logging package Log4j 2 versions 2.14.1 and below (CVE-2021-44228).
Apache Log4j is the most popular java logging library with over 400,000 downloads from its GitHub project. It used by a vast number of companies worldwide, enabling logging in a wide set of popular applications.
Exploiting this vulnerability is simple and allows threat actors to control java-based web servers and launch remote code execution attacks.
The Log4j library is embedded in almost every Internet service or application we are familiar with, including Twitter, Amazon, Microsoft, Minecraft and more.
At present most of the attacks focus on the use of a cryptocurrency mining at the expense of the victims, however under the auspices of the noise more advanced attackers may act aggressively against quality targets.
What do you need to do in order to remain protected?
Check Point already released a new Quantum Gateway protection powered by Threat Cloud, designed to prevent this attack, and by using it- you’ll stay protected.
If your Quantum gateways are updated with automatic new protections, you are already protected. Otherwise, you need to implement a new protection by following the guidelines here. We urge IT and Security teams to take immediate remediation measures on the matter.
Is Check Point affected by the Log4j vulnerability?
The Check Point Infinity architecture is not impacted by the Log4j.
We thoroughly verified that the vulnerability does not affect our Infinity portfolio including Quantum Gateways, SMART Management, Harmony Endpoint, Harmony Mobile, ThreatCloud and CloudGuard.
What’s next?
Check Point Research is thoroughly investigating the Log4j vulnerability
Check Point Research (CPR) closely monitors the massive scans and exploit attempts. While the activity as we write these lines is limited to scanners and mostly crypto mining threat actors, it does not mean more advanced threat actors are just sitting back enjoying the noise activity. In fact, they are acting silently behind the scenes.
It is clearly one of the most serious vulnerabilities on the internet in recent years.
When we discussed the Cyber pandemic, this is exactly what we meant – quickly spreading devastating attacks.
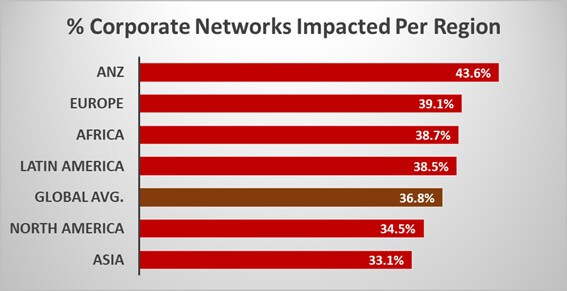
The numbers behind CVE-2021-44228
This CVE joins the general atmosphere of cyber pandemic where major vulnerabilities in popular software and services impact enormous number of organizations.
Since we started to implement our protection we prevented over 820.000 attempts to allocate the vulnerability, over 46% of those attempts were made by known malicious groups.
We have so far seen an attempted exploit on over 36.8% of corporate networks globally