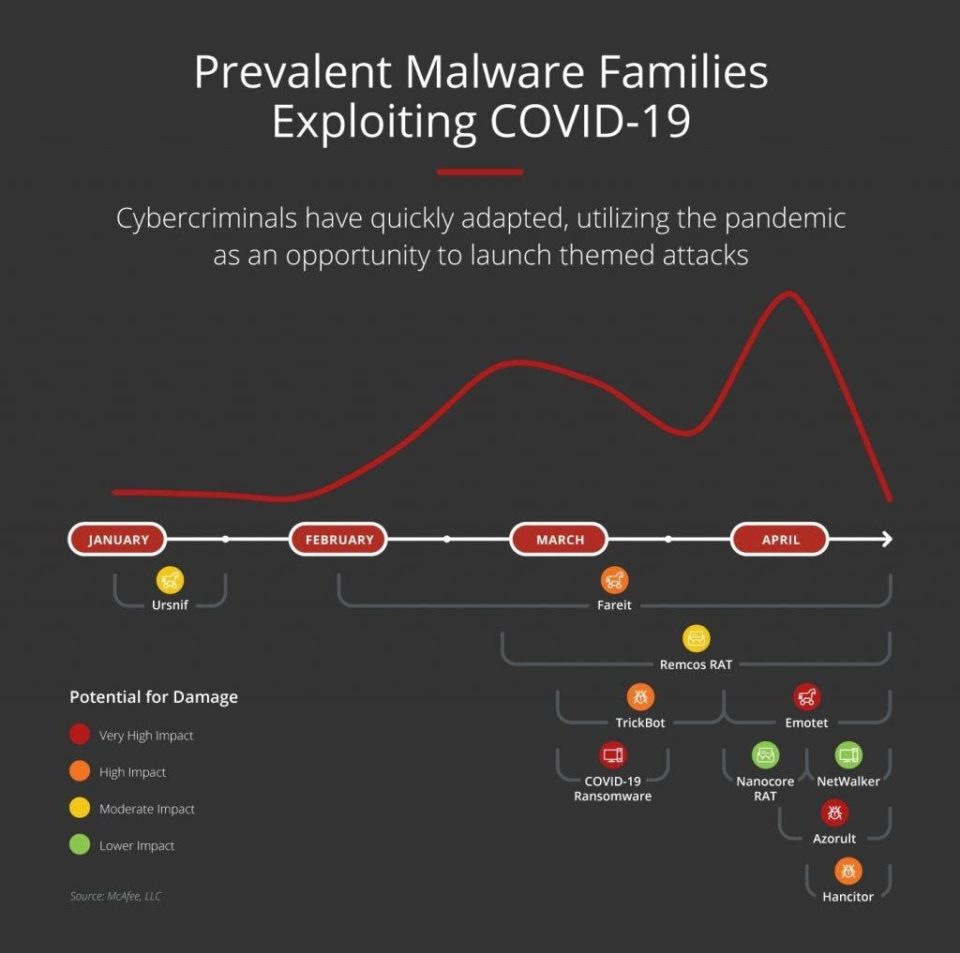
Phishing and Trojans:
In January, McAfee observed the emergence of a phishing campaign using a strain of the Ursnif banking Trojan commonly used to steal usernames, passwords and user behavior information. As bait, the phishing emails used pandemic-themed messaging and a Microsoft Office document with “COVID-19” in its filename to lure users into opening the attachment and releasing the malware onto their computers.
Beginning in February, McAfee observed another campaign leveraging phishing emails referencing the terms “COVID-19” and “Coronavirus” to entice users to click on links or attachments that then downloaded the information-stealing Fareit Trojan onto their computers.
Bogus SBA Loan Emails:
Beginning in late March, a phishing campaign used emails claiming to originate from the U.S. Government Small Business Administration (SBA). These emails appeared to offer small businesses information and guidance on how to apply for SBA loans. In fact, they were a mechanism for infecting unsuspecting small business owners with the information-stealing Remcos Remote Access Tool (RAT)
Scam COVID-19 Tests:
In March, cybercriminals distributed phishing emails appearing to originate from organizations offering COVID-19 testing. Users were prompted to open an attached document, which would then download the information stealing Trickbot malware.
Scam Antibody Research & Treatment:
By late March, McAfee began to see COVID-19-themed phishing campaigns using a strain of the Emotet Trojan to infect users’ systems. One version of this email promises to provide information on Coronavirus antibody research and new treatments for the disease. Once established on the victim’s system, Emotet can do a number of things on the system but it is almost always programmed to propagate itself by sending large numbers of spam emails to other user’s systems.
Precautionary Measures:
April saw the emergence of phishing email campaigns using subject lines such as “COVID-19 Urgent Precaution Measures” to distribute the NanoCore Remote Access Tool (RAT) for exfiltration of valuable information.
Fake John Hopkins Infection Map:
April also saw cybercriminals use phishing emails to promote a fake website featuring a global Coronavirus infection map appearing to provide data from John Hopkins CSSE. Unfortunately, those same emails were used to infect inquisitive users with a strain of information stealing Azorult malware.
Bogus Insurance Invoices:
Mid-April also saw cybercriminals use COVID-19-themed emails from a bogus insurance company to infect users’ systems with fake invoice attachments carrying the Hancitor malware.
COVID-19 Ransomware.:
March saw the emergence of Ransomware-GVZ, a Coronavirus-themed ransomware campaign. Ransomware-GVZ displays a “ransom note” message demanding payment in return for decrypting their systems and the precious personal and corporate data they contain
By mid-April, another ransomware campaign joined the fray, this time using a strain of Netwalker ransomware to infect users via a malicious file named “CORONAVIRUS_COVID-19.vbs”.
Spam & Scam:
Finally, beyond malware, McAfee has detected thousands of COVID-19-themed spam emails and websites scamming victims seeking to purchase medical supplies such as testing kits, face masks, and other protective gear. Over the first 13 weeks of the pandemic, McAfee saw the number of bogus websites increase from 1,600 a few weeks ago to over 39,000.
Takeaways
Cybercriminals will always seek to create ever more sophisticated and opportunistic attacks. Remote work paradigms create new opportunities and require new defense mechanisms and practices. This week’s report illustrates the importance of maintaining strong cybersecurity defenses regardless of whether employees are in traditional office or home-office environments. We must formulate the right combination of technology and education to make that happen.
Organizations need to defend against cyber-threats at home with data protection solutions capable of preventing intellectual property and other forms of sensitive data from being stolen. McAfee is focused on helping address these challenges with its Unified Cloud Edge and CASB solutions that are inherently focused on protecting both mobile and traditional devices from threats and data theft. Additionally, modern endpoint and EDR capabilities are capable of detecting a wide range of threats that place the user and their organization at risk.
The future is uncertain, change and disruption are inevitable, and our adversaries are determined in their drive to exploit us at work, no matter where that may be. We must rise to the challenge of pushing technology forward, adapting, and developing stronger cyber defenses to ensure that the “future of work” is a secure one.