Gemalto & Ponemon Institute Study reveals more than half of companies do not have a proactive approach for compliance with privacy and security regulations for data in cloud environments
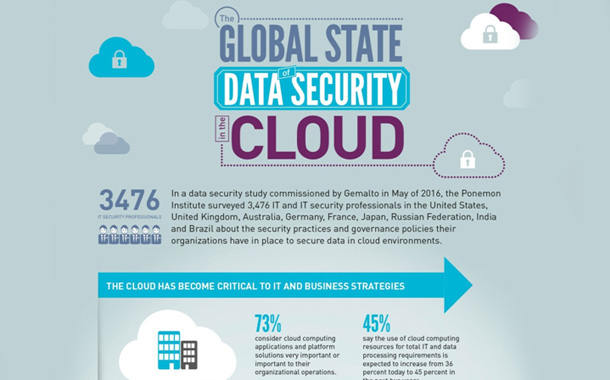
Despite the continued importance of cloud computing resources to organizations, companies are not adopting appropriate governance and security measures to protect sensitive data in the cloud. These are just a few findings a Ponemon Institute study titled “The 2016 Global Cloud Data Security Study,” commissioned by Gemalto. The study surveyed more than 3,400 IT and IT security practitioners worldwide to gain a better understanding of key trends in data governance and security practices for cloud-based services.
According to 73 percent of respondents, cloud-based services and platforms are considered important to their organization’s operations and 81 percent said they will be more so over the next two years. In fact, thirty-six percent of respondents said their companies’ total IT and data processing needs were met using cloud resources today and that they expected this to increase to forty-five percent over the next two years.
Although cloud-based resources are becoming more important to companies’ IT operations and business strategies, 54 percent of respondents did not agree their companies have a proactive approach to managing security and complying with privacy and data protection regulations in cloud environments. This is despite the fact that 65 percent of respondents said their organizations are committed to protecting confidential or sensitive information in the cloud. Furthermore, 56 percent did not agree their organization is careful about sharing sensitive information in the cloud with third parties such as business partners, contractors and vendors.
Dr. Larry Ponemon, chairman and founder, Ponemon Institute said, “”Cloud security continues to be a challenge for companies, especially in dealing with the complexity of privacy and data protection regulations,” To ensure compliance, it is important for companies to consider deploying such technologies as encryption, tokenization or other cryptographic solutions to secure sensitive data transferred and stored in the cloud.”
Jason Hart, Vice President and Chief Technology Officer for Data Protection at Gemalto added, “Organizations have embraced the cloud with its benefits of cost and flexibility but they are still struggling with maintaining control of their data and compliance in virtual environments. It’s quite obvious security measures are not keeping pace because the cloud challenges traditional approaches of protecting data when it was just stored on the network. It is an issue that can only be solved with a data-centric approach in which IT organizations can uniformly protect customer and corporate information across the dozens of cloud-based services their employees and internal departments rely every day.”
According to respondents, nearly half (49 percent) of cloud services are deployed by departments other than corporate IT, and an average of 47 percent of corporate data stored in cloud environments is not managed or controlled by the IT department. However, confidence in knowing all cloud computing services in use is increasing. Fifty-four percent of respondents are confident that the IT organization knows all cloud computing applications, platform or infrastructure services in use – a nine percent increase from 2014.
Only 21 percent said members of the security team are involved in the decision-making process about using certain cloud application or platforms. The majority of respondents (64 percent) also said their organizations do not have a policy that requires use of security safeguards, such as encryption, as a condition to using certain cloud computing applications. Seventy-two percent said the ability to encrypt or tokenize sensitive or confidential data is important, with 86 percent saying it will become more important over the next two years, up from 79 percent in 2014. Sixty-seven percent said the management of user identities is more difficult in the cloud than on-premises.
The new realities of Cloud IT mean that IT organizations need to set comprehensive policies for data governance and compliance, create guidelines for the sourcing of cloud services, and establish rules for what data can and cannot be stored in the cloud. IT organizations can accomplish their mission to protect corporate data while also being an enabler of their “Shadow IT” by implementing data security measures such as encryption that allow them to protect data in the cloud in a centralized fashion as their internal organizations source cloud-based services as needed.