Researchers are still analyzing the unprecedented cyber attack on Cosmos bank that took place between August 10-13, resulting in attackers stealing Rs 94 Crore, approx $13.5 USD. In the first attack on August 11, using stolen card details, approximately Rs. 78 Crore was withdrawn in transactions in 28 countries. This included around 12,000 Visa card transactions. On the same day, approximately, Rs 2.5 Crore was withdrawn through 2,800 debit card transactions in India at various locations. On August 13, the hackers transferred Rs 13.94 Crore into an account in the Hang Seng Bank in Hong Kong by initiating a SWIFT transaction.
An analysis by Securonix estimates that infiltration was executed either by spear phishing, and/or remote administration/third-party interface. Following the initial infiltration, attackers were able to carry out fraudulent ATM transactions, and later, with lateral movement, were able to attack a SWIFT server and transfer funds to a foreign account.
From over 10 years of work with global financial institutions, helping them secure their infrastructure, it is surprising to find that Endpoint Detection and Response (EDR) technology, a prerequisite for securing any banking network, is missing from the security stack of most of the financial organizations we’ve have encountered in India.
EDR is a solution for detecting attacks that aim to penetrate the organization through its endpoints; e.g. workstations, or servers, and is designed to detect advanced and highly evasive attacks by using more advanced detection approaches that include AI, machine learning and behavioral analysis. EDR is essential for financial institutions because banking attackers are the most sophisticated malicious actors. As we’ve seen in the Cosmos attack, they study their targets closely in advance of the attack, determine the weak spots, such as a third-party interface, or a human weakness such as an employee who tends to open phishing emails. Then, they would use evasion tactics to bypass conventional security solutions. EDR leverages an agent installed on the endpoint. The agent continuously records the activity on that endpoint, stores the data on a server, and analyzes the data using AI-based approaches. EDR is designed to be the last line of defense, which detects the attacks that bypassed all other lines of conventional security including firewalls, email security, antivirus and more.
Three ways EDR can help financial institutions avoid becoming the next Cosmos
Here are 3 typical examples for the unique benefits that EDR brings to financial institutions in their battle against sophisticated cyber actors:
- Detecting signature-less attacks
You may have experienced the event when your antivirus blocked a malicious file. The file is identified by its unique “fingerprint” – a signature. If the signature matches that of a known malware file, the file will be blocked and will not run. However, sophisticated attackers will never use a file with a known signature. Instead, they would design and package a dedicated file, previously unused and unknown to security systems. As a result, they easily bypass conventional endpoint security solutions and sandboxes. Based on the current analysis of Cosmos breach, the attackers have likely used advanced evasion tactics and were therefore not detected at the endpoint. Then, they could freely stage their attack inside the network, and move laterally.
Unlike conventional solutions, EDR does not base its detection on signatures. Instead, it uses algorithmic approaches including AI, machine learning and behavioral analysis, to detect suspicious behaviors, for example: an attempt to perform code injection. These behaviors are much more difficult, often impossible, for the attacker to hide.
- Detecting File-Less Attacks: I’ve already mentioned that attackers use sophisticated methods to hide malicious files. But today, evasive attackers are shifting to attacks that do not use files at all. These file-less attacks take advantage of legitimate applications and use them to execute the attack and mask it from security systems. The most commonly exploited application is Windows PowerShell, a Windows command line tool with broad access permissions, which is even white-listed (approved) by Windows Firewall. An attacker running a PowerShell script on a workstation can gain access to sensitive areas of the operating system, gain administrative permissions, and more. Obviously, these attacks cannot be detected by conventional endpoint security or sandboxes, which rely on checking files. Unlike conventional solutions, EDR is not restricted to file-based malware detection. I am not ruling out the option that the attack on Cosmos was file-less, as I’ve seen this approach being used in multiple cases on financial organizations.
- Detecting Low and Slow Attacks
we see an increasing trend where malware compromises an organization, but the actual breach may only be detected only a year or more later, because it is executed slowly, “under the radar” for example by continuously transferring small amounts of funds, too small to raise a concern or a security alert, as demonstrated in this example from Specs, a large retail chain in the US.
EDR, however, does not rely on a single high-profile event to detect, rather, it works by aggregating data into a big-data repository and continuously analyzing it, connecting the dots to build a story – by correlating somewhat suspicious individual activities into an unequivocal coherent multi stage attack. This valuable repository can also serve organizations for proactive threat hunting – allowing their security teams to search for suspicious activity within historical records. This can also be used to detect attackers that still lie low in this organization, based on similar actions they took elsewhere.
SOAR – the Next Step for Financial Institution Cyber-Preparedness
What else can financial organizations do to prepare for the next attack?
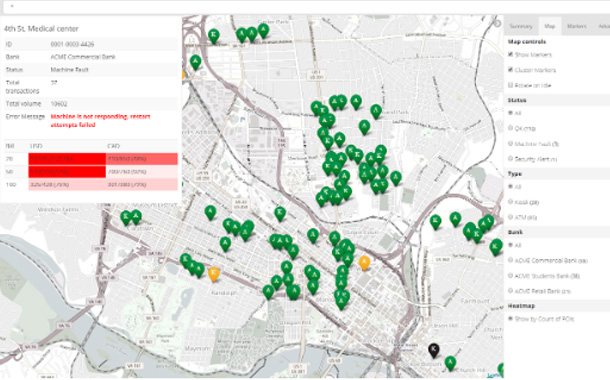
An important next step towards cyber resilience is ramping up your incident response operation and creating clear, repeatable incident response processes, technologies, and the skilled workforce to support it. Start by reading the detailed Reserve Bank of India (RBI) Guidelines. These guidelines require financial institutions to develop and implement processes for preventing, detecting, analyzing and responding to information security incidents. Today, most of these processes can be automated and orchestrated with a SOAR (Security Orchestration, Automation and Response) solution, which dramatically accelerates incident resolution. An advanced SOAR solution can reduce response time by 90 percent. They can even provide dashboards to monitor specific asset like your SWIFT server, and your ATMs, potentially preventing incidents like the Cosmos attack.
ATM Security Status – Cyberbit SOAR Solution
Summary
Financial organizations all over the world are realizing that attackers are willing to spend increased time and resources on attacks that are tailored to bypass security systems. Therefore, these organizations are setting up new security systems that focus on advanced, AI-based detection systems, threat hunting, and automated incident response, powered by technologies like EDR and SOAR. They use advanced platforms such as Cyber Ranges, to train their teams and keep them skilled. BFSI organizations in India must now catch up, sooner rather than later, so we can avoid another Cosmos attack.
By: Edy Almer, VP Product at Cyberbit




