Phorpiex, an old threat known since 2016, was initially known as a botnet that operated using IRC protocol (also known as Trik). In 2018-2019 Phorpiex switched to modular architecture and the IRC bot was replaced with Tldr – a loader controlled through HTTP that became a key part of the Phorpiex botnet infrastructure. In our 2019 Phorpiex Breakdown research report, we estimated over 1,000,000 computers were infected with Tldr.
Simultaneously, the C&C servers started distributing a bot that had never seen before. It was called “Twizt” and enables the botnet to operate successfully without active C&C servers, since it can operate in peer-to-peer mode. This means that each of the infected computers can act as a server and send commands to other bots in a chain. As a really large number of computers are connected to the Internet through NAT routers and don’t have an external IP address, the Twizt bot reconfigures home routers that support UPnP and sets up port mapping to receive incoming connections. The new bot uses its own binary protocol over TCP or UDP with two layers of RC4-encryption. It also verifies data integrity using RSA and RC6-256 hash function.
Malware prevalence and targets
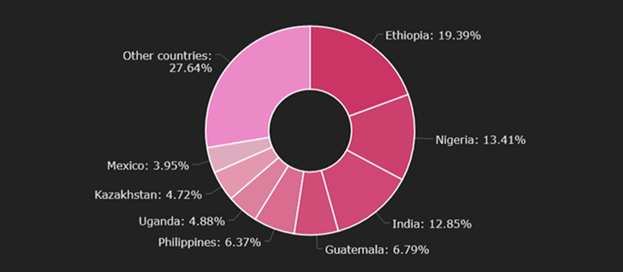
In our telemetry throughout the year, we saw an almost constant number of Phorpiex victims, which persisted even during periods of the C&C servers’ inactivity. The numbers began to increase over the last 2 months. In 2021, Phorpiex bots were found in 96 countries. Most Phorpiex victims are located in Ethiopia, Nigeria and India:
Thousands of victims, hundreds of thousands dollars lost
Aside of the new version of the bot, the methods of monetization have not changed. In our previous research, we focused on sextortion campaigns and cryptocurrency mining. At that time, Phorpiex’s revenues from crypto-clipping were not very significant.
So, what is crypto-clipping? Cryptocurrency clipping (or crypto-clipping) is stealing cryptocurrency during a transaction, by substituting the original wallet address saved in the clipboard with the attacker’s wallet address. When we browse the Internet, we use human-readable domain names that are easy to remember. However, in all popular blockchains there are no analogues for domain names, and the addresses are too long to be typed manually.