IoT is everywhere. From smart light bulbs to IP cameras, wearables, and even smart kitchen appliances, IoT provides benefits for any organization as it enables employees to be more productive and crucial business processes to run more smoothly, intuitively, and efficiently. So much so, that IoT revenue is expected to grow to $549 billion in 2022 and the number of connected IoT devices is expected to reach $15.9 billion by 2030. (CompTIA)
However, the rush to bring this IoT technology to market also increases the cyber-attack surface for organizations when the security of these assets is overlooked. According to Gartner, more than 25% of all cyberattacks against businesses will involve IoT in some way. Closer to the home, in India an organization is being attacked on an average 1797 times per week in the last 6 months, compared to 1564 attacks per organization in APAC, as outlined in Check Point’s Threat Intelligence report. Apart from this, in India, the average weekly impacted organizations by mobile malware stood at 4.3 percent as compared to the APAC average of 2.6 percent.
Innovative security vendors that are always thinking toward the future, like Check Point, are determined to keep users protected at all costs.
This blog will explore a real-life use case in which Check Point’s Quantum IoT Protect solution identified a risky device and protected the organization from a devastating cyberattack. But first let’s quickly recap why these devices are vulnerable by design. Summarizing a previous blog, we released on IoT a few months back: IoT devices, often, come to market with a intrinsic flaws that make them a security risk:
- Lack of standardization creates a hodgepodge of devices
- Weak security approach, including weak or nonexistent passwords
- Outdated and unpatchable hardware, firmware, or software
- Larger number of devices which expands the attack surface
As a result, it’s all too easy for hackers to gain access to these devices and either wreak havoc with the IoT devices themselves or move laterally to harm mission-critical systems and steal the personally identifiable information (PII) of customers or employees, intellectual property, or other assets. Hackers may also gain control over the network and hold it for ransom. And their latest trick? Combining these strategies in double extortion attacks that promise even more lucrative payoffs.
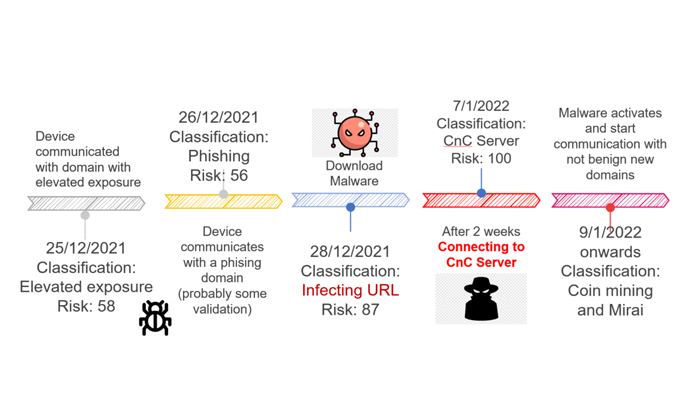
The Investigation
Early in the investigation, the Check Point team determined that the device was communicating with a few domains that had a high-risk score reputation. Further investigation of these events led to a conclusion that the device was communicating with one or more Command & Control (C&C) servers.
The response team confirmed that this IoT device was infected with Mirai and crypto mining bots. Further log analysis demonstrated exactly how the device became infected and identified different steps of the infection and was able to describe to the customer where they fell on a Cyber Kill Chain timeline.