Kazi Nazrul Islam, Sr.Consultant Cyber Security, PricewaterhouseCoopers(PwC)
Information plays a key role and almost every Information-based organizations and their Information systems are today equipped with preventive control such as firewalls, IDS/IPS systems, SIEM,WAFs,anti-malware and DLP systems. However, the number of security breaches and cost of the data loss Increasing year over year. This has forced organizations to shift their focus from preventing attacks to rapid threat detection and response.
Threat prediction and detection requires collection and analysis of the vast amount of data. This has become a huge challenge for organizations due to the volume and nature of log data produced by different security controls and other Information systems Including IT equipment, Applications and servers. Centralize monitoring, storage sorting and analysis of collected data produced by different security controls and other Information including IT equipment, applications and servers. Centralized monitoring,storage,sorting and analysis of collection data to draw actionable threat Insight has become a daunting task and requires specialized processes and technology. There is huge demand for professionals with the right set of skill ranging from knowledge of processes and technology to analytics to deal with huge volume of data threat Inelegance. Rapid threat detection and response is possible when an Organization adopt a proper security operation strategy.
Management of security operation center:
A Management of security operation center is a collection of systematic and repetitive set of Interconnected security activities that help the organization to maintain their security posture to an adequate level. It is an ongoing effort that focuses on both physical safety and digital security assets. Beardly, A security operation management comprises different security activities like as
Security Infrastructure: Related to perimeter,networks,endpoint,application and data by Implementing adequate preventive, detective and corrective Information security controls.
Security Prevention: like as vulnerability management and penetration testing ensuring security in the network against vulnerabilities and threats.
Compliance and validation: Various governance risk and compliance programs help the Organization to continue its business without any risk . some governance risk and compliance programs Involve ISO27001 reediness Assessment, Security baseline policy document for ISMS and so on.
Security Operations: This operation performed by real-time security alerting, threat analysis& Intelligence and preemptive Incident reporting, detection and response. A SOC should have the preventive, detective, responding and reporting capabilities.
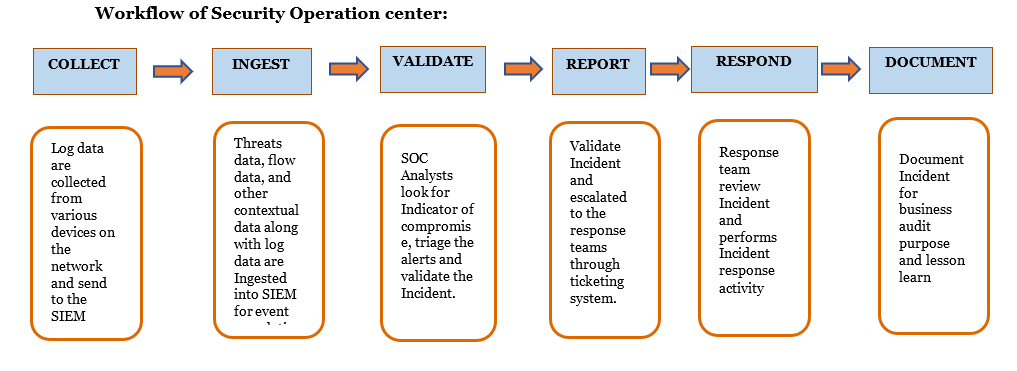
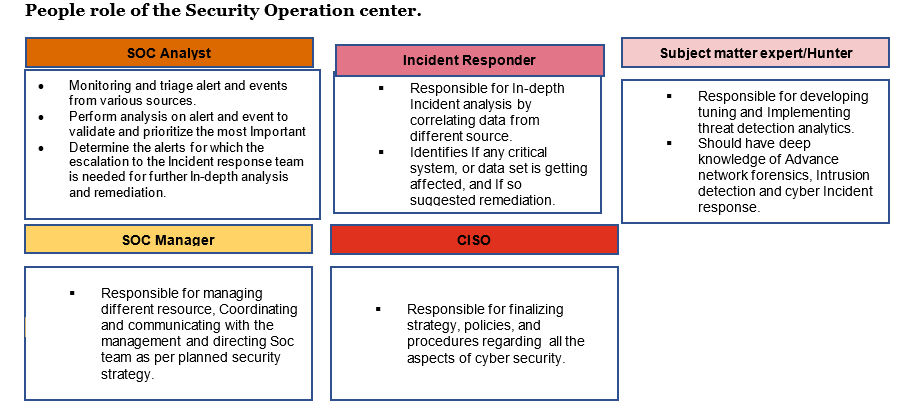
A security Operation center requires cooperation and communication among people, process and technology to collect, sort and Investigate security events. People are the security talent who are responsible for the executing the functions. They may be security operators,analysts,or pen testers and may be Internal or outsourced.
Processes: Process is the Important part of the Security operation center. A right team will perform the right tasks through a well-defined process. Process are used by the different functional parts of the SOC to perform seamless and effective operations. They behave as a link between people and technology.
Typical processes Involved in SOC:
- Business Processes
- Technology processes
- Operational processes
- Analytical Processes
Technology: A organization should always select the technology which works for people and process. Technology plays Important role in the security operation center. Both Multidimensional and multilevel technology should participate in an efficient manner to protect the systems, programs, and solutions from unauthorized access for a longer period of time. It may Include SIEM solutions,Intrution detection system,Intrution prevention system,firewall,database activity monitoring,Deshboard,Ticket system, and automated assessment tools.
Challenges in Implementation of Security Operation center: SOC has the Following Challenges that come in between its Implementation.
- SOC is receiving a large number of security alerts due to which major amount of SOC analyst time is wasting in triage and validating authenticity of alerts.
- SOC is using wider range of security tools which are difficult to monitor and manage Individually.
- Lack of skill analyst difficult to handling of security Incident.
- Always meeting the legal and regulatory requirement little bit challenges
- It is very difficult to manage and Implement Large number of process and procedure.




