Akamai Releases First Quarter 2017 State of the Internet / Security Report; Report highlights a 35 percent year-over-year increase in total web application attacks from Q1 2016
Akamai Technologies released its First Quarter, 2017 State of the Internet / Security Report. The report, using data gathered from the Akamai Intelligent Platform, provides analysis of the current cloud security and threat landscape, as well as insight into attack trends.
“If our analysis of Q1 tells us anything, it’s that risks to the Internet and to targeted industry sectors remain and continue to evolve” said Martin McKeay, senior security advocate and senior editor, State of the Internet / Security Report. “Use cases for botnets like Mirai have continued to advance and change, with attackers increasingly integrating Internet of Things vulnerabilities into the fabric of DDoS botnets and malware. It’s short sighted to think of Mirai as the only threat, though. With the release of the source code, any aspect of Mirai could be incorporated into other botnets. Even without adding Mirai’s capabilities, there is evidence that botnet families like BillGates, elknot, and XOR have been mutating to take advantage of the changing landscape.”
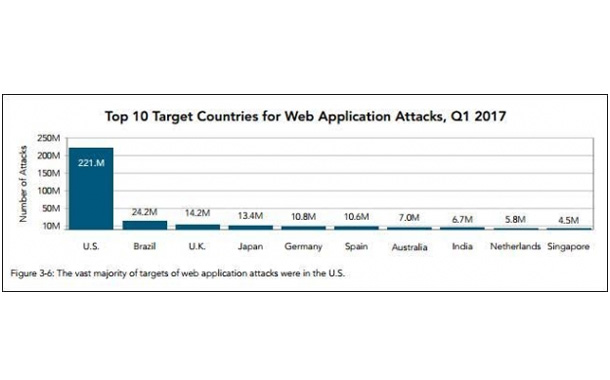
The United States remained the top source country for web application attacks, showing another significant year-over-year increase — up 57 percent from Q1 2016. The top three attack vectors used against web applications in Q1 of 2017 were SQLi, LFI and XSS. The Netherlands, in second for the top source of web application attacks of Q1 2017, dropped to 13 percent from 17 percent in the previous quarter, remaining a consistent source of attack traffic and a large proportion of attacks from a country of only 17 million citizens.
UDP fragment, DNS and NTP maintained their positions as the top three DDoS attack vectors, while reserved protocol floods and connection floods were also on the Q1 2017 attack vectors list. The Q1 2017 top three most frequent attack vectors per week were ACK, CHARGEN, and DNS.
New reflection attack vector Connectionless Lightweight Directory Access Protocol (CLDAP) was discovered and has been observed producing DDoS attacks comparable to DNS reflection with most attacks exceeding 1 Gbps.
“If anything, our analysis of Q4 2016 proves the old axiom ‘expect the unexpected’ to be true for the world of web security,” continued McKeay. “For example, perhaps the attackers in control of Spike felt challenged by Mirai and wanted to be more competitive. If that’s the case, the industry should be prepared to see other botnet operators testing the limits of their attack engines, generating ever larger attacks.”