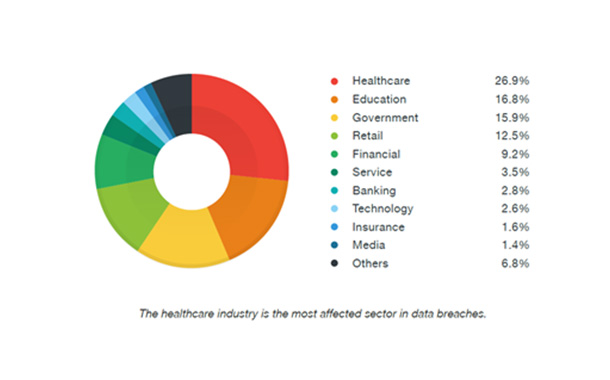
Research report by Trend Micro reveals the healthcare industry (26.9%) is the most affected sector in data breaches followed by Education (16.8%), Government (15.9%), Retail (12.5%) and Finance (9.2%)
Several high-profile organizations came under fire in 2015 when channelized breaches led to the exposure of critical data and put their clients and employees at risk. Although incidents of this magnitude have become common, as of last year, Trend Micro noted the more active use of compromised data for online extortion and cyberattacks. Under data breaches, the healthcare industry (26.9%) is the most affected sector in data breaches, followed by Education (16.8%), Government (15.9%), Retail (12.5%) and Finance (9.2%) sectors.
The Trend Micro Smart Protection Network blocked over 52 billion threats in 2015, a 25% decrease from 2014. This decrease is consistent with the downward trend of system infections since 2012, caused by attackers who have become more selective of their targets as well as the shift in technologies they use.
According to the release, protected health information (PHI) of 80 million Anthem consumers, including names, addresses, birth dates, income data, and Social Security numbers were compromised. Breaches have also found their way to the federal level. These high-profile incidents are consistent with our data breach analysis. Other sectors also include education, retail, and finance.
Remote device wipe, disk encryption, the use of virtual infrastructure, and enforcement of stricter policies can help mitigate such cases. But for those that involve malware and hacking, breach detection and network security solutions are required. System administrators and managers need solutions that allow them to monitor network traffic across all ports to spot any anomalies and prevent attackers before they can advance. Custom sandboxing, on the other hand, would give them the capabilities needed to single out malware, identify C&C activity, and pinpoint other tell-tale signs of impending or ongoing attacks.