Without HTTPS, with HTTP attackers can access website accounts and sensitive information and inject malware or other malicious files into a website and resulting into attacks of vivid nature.
This article is something most of us already know but fail to comply and end up compromising our privacy, confidential data or financial losses.
Hyper Text Transfer Protocol Secure (HTTPS) is the secure version of HTTP, the protocol over which data is sent between your browser and the website that you are connected to. The ‘S’ at the end of HTTPS stands for ‘Secure’. It means all communications between your browser and the website are encrypted.
HTTPS protects against man-in-the-middle attacks, eavesdropping, tampering with contents of communication between a website and users. On the other hand, HTTP (Hyper Text Transfer Protocol) do not secure communication taking place between two ends, leaving it vulnerable to such attacks.
Without HTTPS, with HTTP attackers can access website accounts and sensitive information, and inject malware or other malicious files into a website and resulting into attacks of vivid nature.
- Denial-of-service (DoS) and distributed denial-of-service (DDoS) attacks.
- Man-in-the-middle (MitM) attack.
- Phishing and spear phishing attacks.
- Password attack.
- SQL injection attack.
- Cross-site scripting attack.
- Eavesdropping attack.
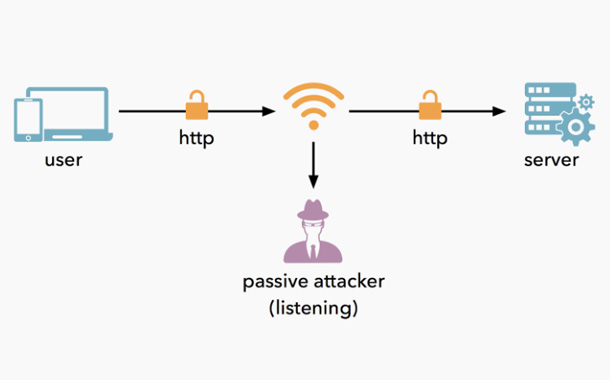
So, Payment and other sensitive transactions were the first to be secured using HTTPS connections. As of now, it has become increasingly important to protect all types of sites irrespective of what the content of the website is.
By securing the website, you would not just be safeguarding the website, but also protecting the privacy of website users’ communications, information and identities.
HTTPS (Hyper Text Transfer Protocol Secure) appears in the URL when a website is secured by an SSL certificate. The details of the certificate, including the issuing authority and the corporate name of the website owner, can be viewed by clicking on the lock symbol on the browser bar.
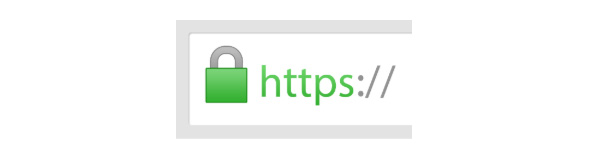
This lock is very important. It indicates that your browser has used HTTPS to properly secure and authenticate your connection with a website. HTTPS has three main goals:
- Privacy: Encrypting data such that anything in-between your browser and the website cannot read your traffic.
- Integrity: Ensuring that the data received on either end has not been altered unknowingly along the way.
- Authentication: Proving that the website your browser is talking to is who they say they are.
SSL and TLS are both cryptographic protocols that provide authentication and data encryption between servers, machines and applications operating over a network (e.g. a client connecting to a web server). SSL is the predecessor to TLS. … TLS is currently at v. 1.3
SSL stands for Secure Sockets Layer and, in short, it’s the standard technology for keeping an internet connection secure and safeguarding any sensitive data that is being sent between two systems, preventing criminals from reading and modifying any information transferred, including potential personal details. The two systems can be a server and a client or server to server.
SSL uses encryption algorithms to scramble data in transit, preventing hackers from reading it as it is sent over the connection. This information could be anything sensitive or personal which can include credit card numbers and other financial information, names and addresses.
Such secured connection offers several benefits:
- Safeguarding sensitive data being transferred between browser and server.
- Preventing criminals or any intruder from reading the information transferred.
- Avoiding misuse of vital information like credit card numbers, financial information, addresses and names.
- Safeguarding the information transferred from unwanted modification.
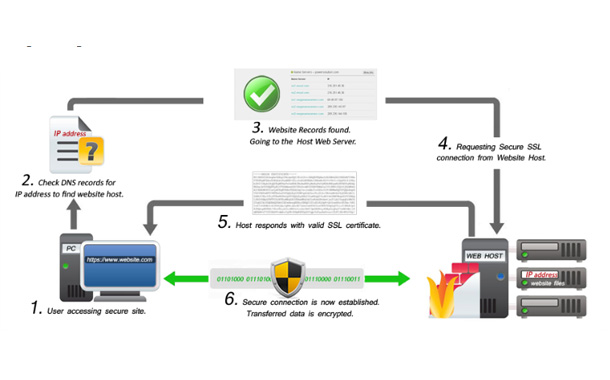
The SSL certificate is issued by a trusted third party, typically a trusted Certificate Authority (CA). It helps to ensure that you are dealing with the right website or person through a secured connection.
Essentially, an SSL certificate links the domain, server or host name to an organization’s identity and location. The certificate is installed into the organization’s web server, and when user accesses secured website, it gives secured connection between the user browser and the server.
Information about the owner contained in a certificate, includes:
- Issued to
- Issued from
- Start date
- Expire date
- Domain name
- Certificate authority name
TLS (Transport Layer Security) is just an updated, more secure, version of SSL.
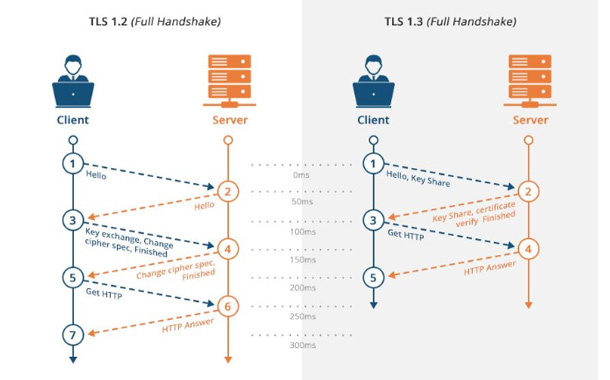
What makes TLS 1.3 less vulnerable than TLS 1.2 is the complete removal of support of older, broken forms of cryptography. This means there’s literally no potentially vulnerable stuff that hackers can turn on. The features in TLS 1.2 which were associated with high profile attacks were all removed.The more streamlined TLS 1.3 makes the protocol much faster, giving users a better web browsing experience.
In summary, majority of mishaps happens whilst some bad guy vishes to phish and we fail to pay proper attention to facts and details. In other words, phishing attacks, data breaches, cyber frauds have prime reason of improper attention to the details compared to keeping the fortress strong walled. Simple precaution of watching out on ‘S’ – ‘green padlock’ on the websites we visit may help to an extent.
Credits – Internet
About the author:
Archie Jackson, AVP – Technology/Information Security, Genpact
Archie Jackson is a curious, incisive & visionary senior technology professional with 17+ years of insightful experience in IT Infrastructure design, implementation and operations with strong service management, leadership and digital transformational skills. He carries good knowledge of ‘Software defined’ & ‘hyperconverged compute, storage, networks and virtualization with collaborative communication methods. He is highly sensitive towards Cybersecurity/Information Security. He is a Six Sigma Green Belt too.




