Information is a valuable asset to both small and large businesses. It can make or break the business. When properly managed it allows to operate with confidence and ISO/IEC 27001 brings equal benefits to organizations of all sizes.
ISO 27001 is an internationally recognized Standard that describes best practice for an Information Security Management System (ISMS). It encompasses people, process & technology and provides a risk-based approach to Information Security Management. The Popularity of ISO 27001, the International Best Practice Information Security Management Standard, has increased significantly over the past ten years. The result from the most recent ISO Survey show a 14 % increase of Certificates on the previous year.
[quote font=”tahoma” font_size=”13″ font_style=”italic” color=”#262626″ bgcolor=”#f2f2f2″]
“The value of ISO 27001 to any business lies in the fact that, firstly, it is a management standard and secondly, that it looks at information security from a holistic point of view.”
Sudipta Biswas
Vice President & CISO
Prime Infoserv
[/quote]
Information is a valuable asset to both small and large businesses. It can make or break the business. When properly managed it allows to operate with confidence and ISO/IEC 27001 brings equal benefits to organizations of all sizes. Information security management gives SMEs the confidence to meet expectations – from legal to new business opportunities – giving a solid and secure base to grow from.

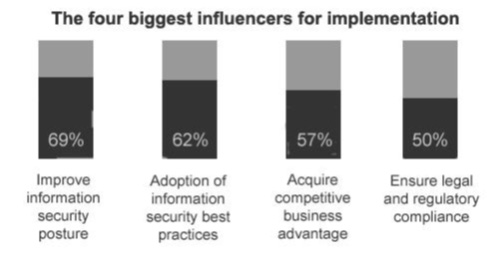
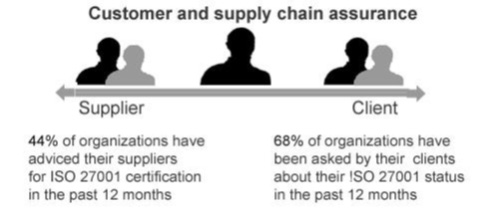
The value of ISO 27001 to any business lies in the fact that, firstly, it is a management standard and secondly, that it looks at information security from a holistic point of view. ISO 27001 encompasses people, processes and Technology, in recognition that information security is not just about Antivirus software, Firewall or any other Security Tools, but depends on the effectiveness of organizational processes and the people who manage and follow them.
Some of the Key Benefits on the ground:
- Identify risks and put controls in place to manage or eliminate them
- Flexibility to adapt controls to all or selected areas of business
- Improved information security awareness amongst all relevant parties
- Gain stakeholder and customer confidence that their data is protected
- Demonstrate compliance and gain status as preferred supplier
- Build trust and credibility in the market to help win more business
- Substantial increase in availability of IT system
- Efficient Capacity planning & IT Infrastructure Augmentation
- Ensures information is protected & available to stake holders
- Visible improvement in Business Continuity
- Cost savings by minimization of incidents




