LAW AND ORDER: POLICIES, PROCEDURES, STANDARDS, AND GUIDELINES
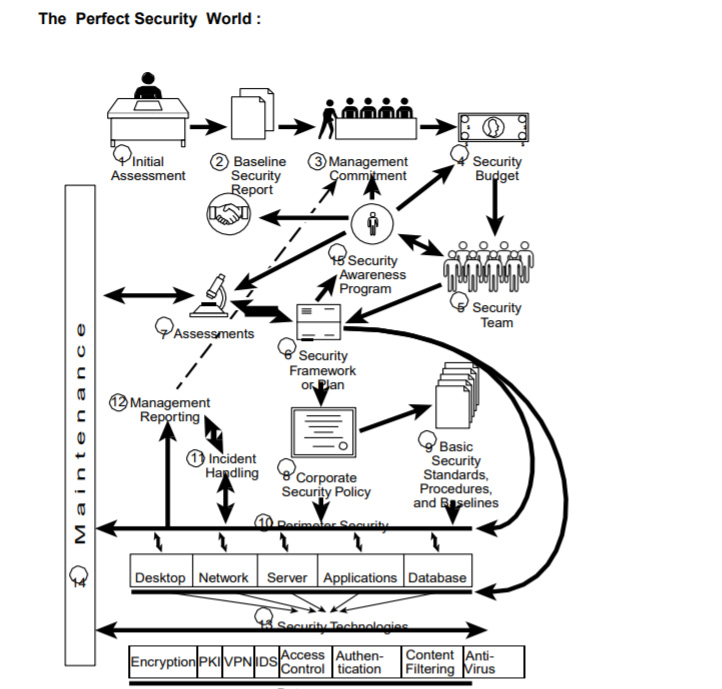
Every world needs some form of law and order. Corporate security policy provides the backbone, the roadmap or recipe for this Security Framework. It defines where a company is and where it wants to go. It establishes baselines to which business processing must adhere to. The baselines are the prescribed security controls specified for each component (hardware/software) in the data processing environment in order to achieve a reasonable and consistent level of security throughout the organization.
Guidelines are documented in such places as the Common Criteria, Policy and procedures are living documents that change constantly as technology evolves or as business needs change. There are differing layers of policy. The higher-level policy should be reasonably generic and cover such items as “It is the policy of Company X that all computer systems will maintain virus scanning tools with up-to-date virus signatures.” This is a management statement of direction. At a lower level are more technical statements or standards that spell out the specific virus scanning software on which the company has standardized. This is the company virus scanning standard. Procedures are the step-by-step actions to support policy and will identify the specifics of how to maintain the virus signatures or use the standard virus tool. These lower-level policies must be maintained and must evolve, always having the support of management and company commitment for consistent enforcement. Higher-level policy is less likely to change but, nonetheless, must be regularly reviewed and even tested to see if it is still applicable to the organization’s business model. Policy, just like program code, should have version control, with old versions archived for future reference, management review, and authorizations (sign-off) for implementation. These are the essential components of basic change management.
Compliance:
Compliance plays a Vital Role in maintaining security framework. Availability of robust Security Policies, Procedures & Guidelines does not ensure they are being followed to prevent any security pit fall. Even availability of best of the breed Security Tools & solutions does not mean that they have been configured properly, patched and maintained at regular interval. Hence Information systems should be regularly checked for compliance with security implementation standards.
Technical compliance checking involves the examination of operational systems to ensure that hardware and software controls have been correctly implemented. This type of compliance checking requires specialist technical personnel & should be performed manually supported by appropriate software tools, if necessary. Compliance checking, for example, Penetration testing which should be carried out by independent experts specifically trained for this purpose. This can be useful in detecting vulnerabilities in the system and for checking how effective the controls are in preventing unauthorized access due to these vulnerabilities. Compliance with legal requirements should be ensured to avoid breaches of any criminal and civil law, statutory, regulatory or contractual obligations and of any security requirements. Hence the design, operation, use and management of information systems may be subject to statutory, regulatory and contractual security requirements.
Critical success factors
Experience shows that the following factors are often critical to the successful implementation of information security within an organization:
- Security policy, objectives and activities that reflect business objectives;
- Visible support and commitment from Management;
- A good understanding of the security requirements, risk assessment and risk management;
- Distribution of guidance on information security policy , procedure and standards to all employees and contractors;
- Providing appropriate Training and Education
- A comprehensive and balanced system of measurement to evaluate performance in information security management and feedback suggestions for improvement.
SUMMARY
Learn from the mistakes of others. You will not live long enough to make all of them yourself. One needs to learn from past mistakes. Not patching or performing maintenance on hardware and software leaves them vulnerable to the same unauthorized access. Known vulnerabilities are a primary cause of unauthorized access and jeopardize the stability of the processing environment.
There are eight layers of vulnerability. These layers fit neatly into physical, technical, and administrative layers. Detail vulnerabilities can be found in each layers of the OSI Reference Model: physical, data link, network, transport, session, presentation, and application, plus the toughest to control layer of vulnerability, the user, who is probably the greatest exposure.
Creating a perfect security environment requires attention to all of the layers that make up a business-processing model. Each layer can introduce unique vulnerabilities. The complete solution is not just about technology. Administration, Management, Policies and process are all important parts of the security solution. Understanding the overall security process can help build a comprehensive security framework. It will have management’s commitment, an adequate budget, and a roadmap called policy with a security awareness program that educates, communicates, and ties everything together by providing feedback to the User as well as management to keep the cycle of security flowing.
By: Sudipta Biswas, Vice President and CISO, Prime Infoserv




